Restrict Access to the /public Container
The /public container (located under the top-level root container) is available by default in FlowForce Server. It acts as a location accessible to any FlowForce Server user and a location where any FlowForce Server user can store their data, without any predefined permissions. Therefore, by default, the /public container has the following permissions.
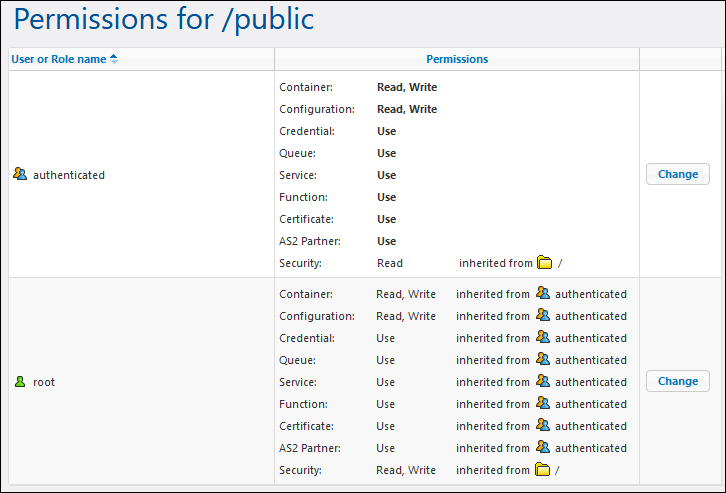
Default permissions of the /public container
This means that, by default, any FlowForce Server user who is member of the  authenticated role can do the following:
authenticated role can do the following:
•Add, modify, and delete objects inside the /public container (namely, jobs, credentials, or other containers)
•Reuse any credentials available in the /public container
•Access as a Web service any job located in the /public container, provided that the job was configured to be available as a Web service
•Refer to any function available in the /public container
•Read the permissions assigned to the /public container
Note: These permissions may also be inherited by any containers that are children of the /public container. Normally, any new container inherits the permissions of the parent container; however, permissions may have been overridden by the  root user, or by other users with relevant privileges.
root user, or by other users with relevant privileges.
You can restrict access to the /public container, if required. Note, however, that the job configuration examples included in this documentation assume the existence of the /public container.
To restrict access to the /public container:
1.Revoke permissions on this container from the  authenticated role (see Setting Container Permissions).
authenticated role (see Setting Container Permissions).
2.Create a new role and assign this role to all users who require permissions to the /public container (see Roles).
3.Assign to the new role only the required permissions (again, see Setting Container Permissions).